Postman is without doubt a handy tool when it comes to API testing. Often I get new API's which I need to test out before implementing them. Most of those API's are JSON or XML and Soap based. First thing is allways throwing the examples at postman and try out the APIs test endpoint.
Most of JSON API's use a bearer token to authenticate, you one just has to set theAuthorization header which shouldn't need explaining.
Some SOAP API are still using username and password within aSecurity envelope, which are part of the body.
All those scenarios are very easy to test in postman. However, Postman has its own feature just for authentication. Because postman is essentially browser based (looks like an electron appto me), I thought it would be nice to have the same user grant flow as I recently tested.
In this previous post, I was implementing theauthorization code flow with proof key for code exchange with a local standalone keycloak server on my nuxt single page app.
I am not going over the setup again, as I already described it, I am just going to share the steps involved to use the exact same configuration to authenticate postman on the same keycloak server, even using the same client.
Postman authenticate with 'authorization code flow and pkce'
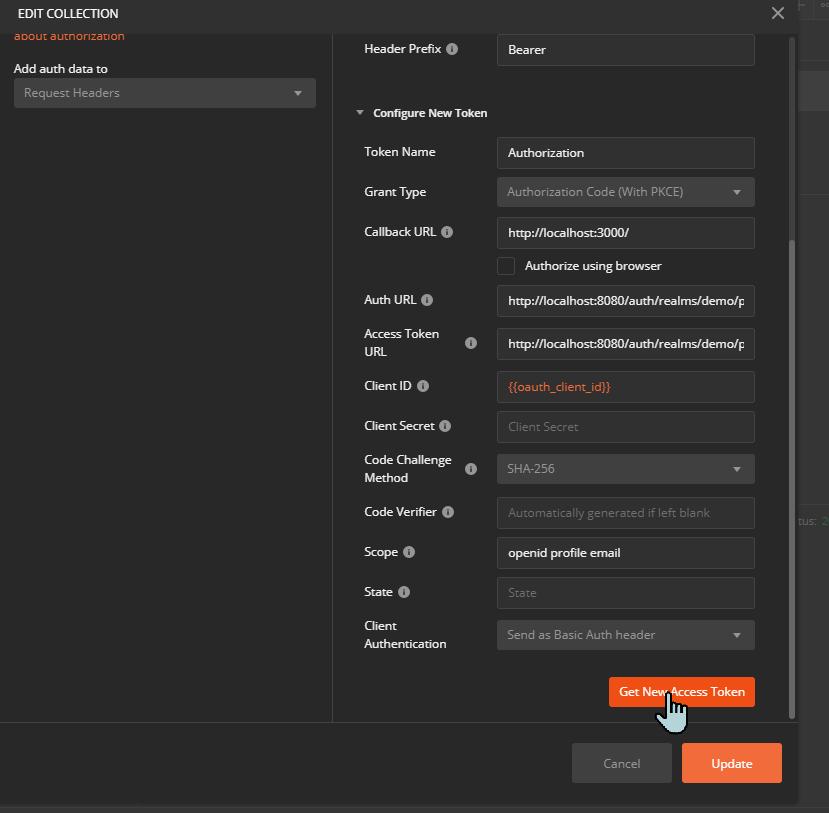
Create or edit a collection
In the collection, choose the Authorization tab and configure the settings as seen in the screenshot.
The same setting are available for single requests, but doing so in the collection lets us inherit the authentication to its requests.
Provide your credentials
If the configuration provided is correct, you are prompted for your credentials in a new window. Fill in the form, postman will catch the redirection on success and return with the authorization token. Additionally, the refresh token is provided as well.
Be aware, postman will not automatically regenerate the authorization token with the refresh token, but you can renew it within postman as long as the refresh token is not expired.
Technically, postman could grap your credentials, so I advise to use this only with test credials on localhost.
Keycloak is keeping a short default expiration time, which is good on production, but maybe anoying testing in postman on localhost. You can easily increase the default timeout of 5min (300s) in your keycloak settings.